A digital solution that exchanges data over the Internet needs to consider three main security risks:
- confidentiality (vs unauthorized access)
- integrity (vs malicious corruption)
- availability (vs interference)
The main techniques developers use to help protect against these threats are:
- encryption (via decryption key)
- authorization (via signature, code or token)
- checksums (checking for data corruption)
- hashing (checking for malicious interference)
Process of verifying someone is who they say they are. Methods include:
- Username / password
- One-step / two-step
- Digital signatures
- Digest Access Authentication - MD5(username:realm:password) .. Produces a hash
- XML signature - <signature><method><hashvalue> … etc
- Application tokens
- OAuth2: authentication protocol that allows you to approve one application interacting with another on your behalf without giving away your password
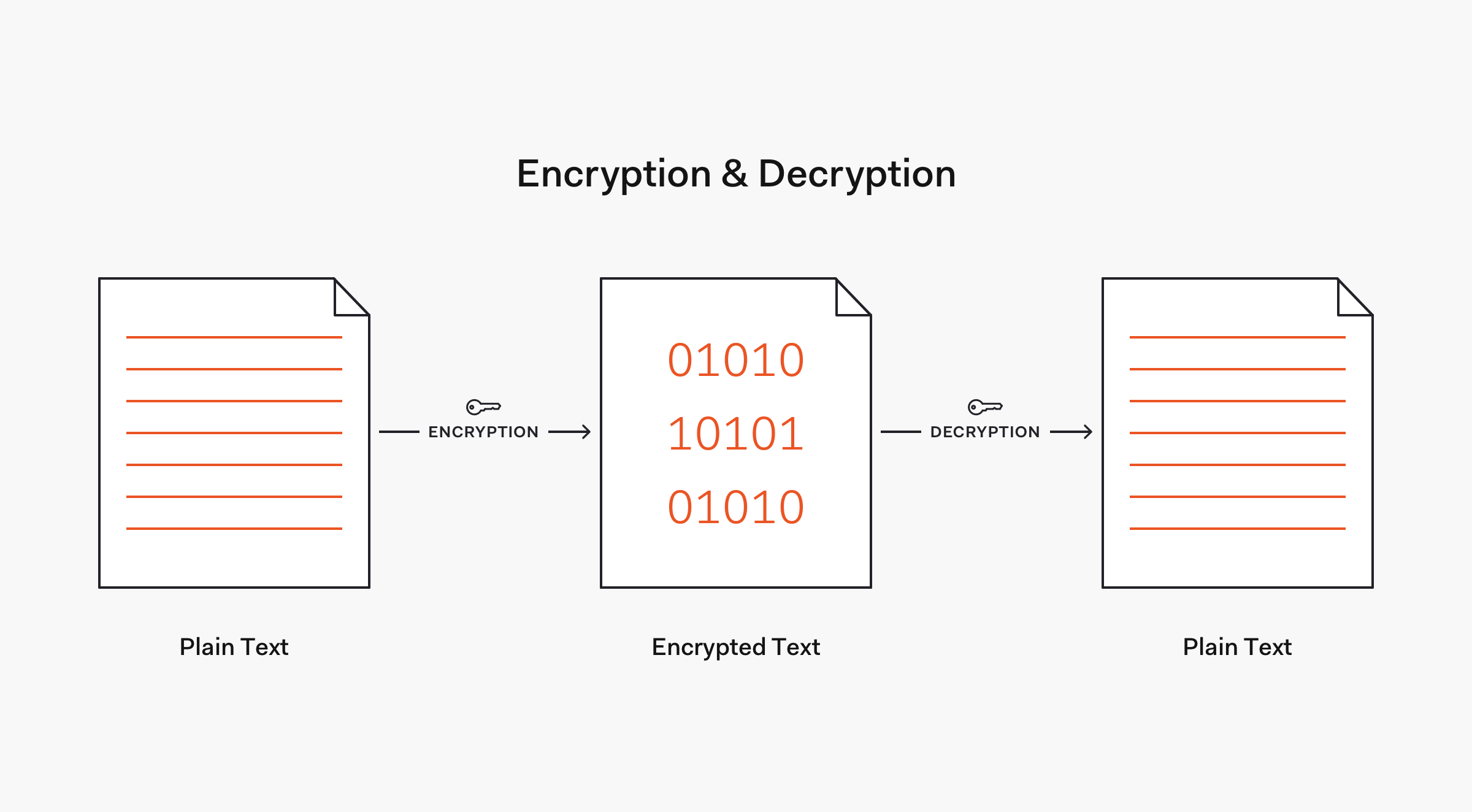
the process through which data is encoded so that it remains hidden from or inaccessible to unauthorized users. It helps protect private information, sensitive data, and can enhance the security of communication between client apps and servers.
Encryption transforms data in an unreadable format.
- plaintext (unencrypted data)
- ciphertext (encrypted data)
- encryption or decryption process (algorithm)
- key (used in the encryption and decryption process)
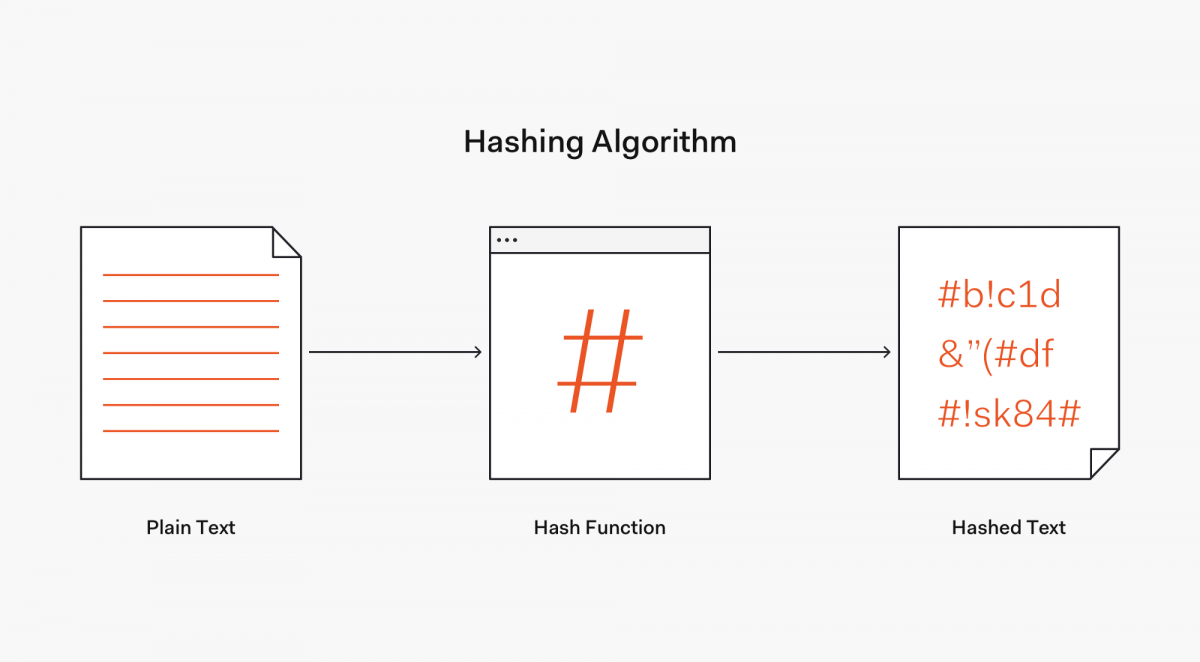
Successful hash characteristics:
- Reliability
- The same text should produce the same identical hash digest every time
- One-way
- Can’t reverse engineer text from hash digest
- Collision resistance
- No 2 hash digests should be alike
- Speed
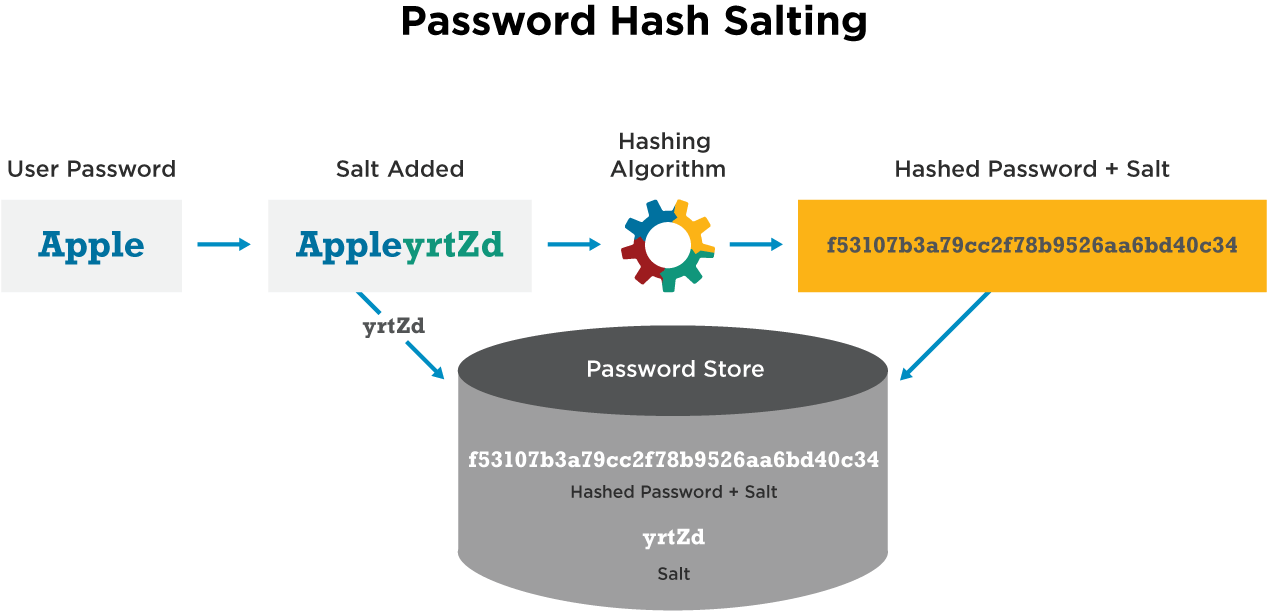
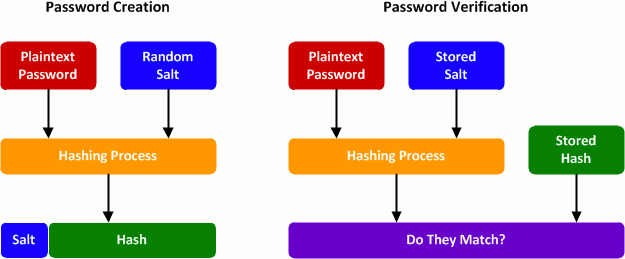
Salts (unique value that can be added to a word before hashing) can prevent pre-computed hash matching. Examples of hash algorithms include MD5 and SHA (SHA-1, SHA-256, SHA-512)
This is a test. >> MD5 HASH CHECKSUM >> 120EA8A25E5D487BF68B5F7096440019
This is a test >> MD5 HASH CHECKSUM >> CE114E4501D2F4E2DCEA3E17B546F339
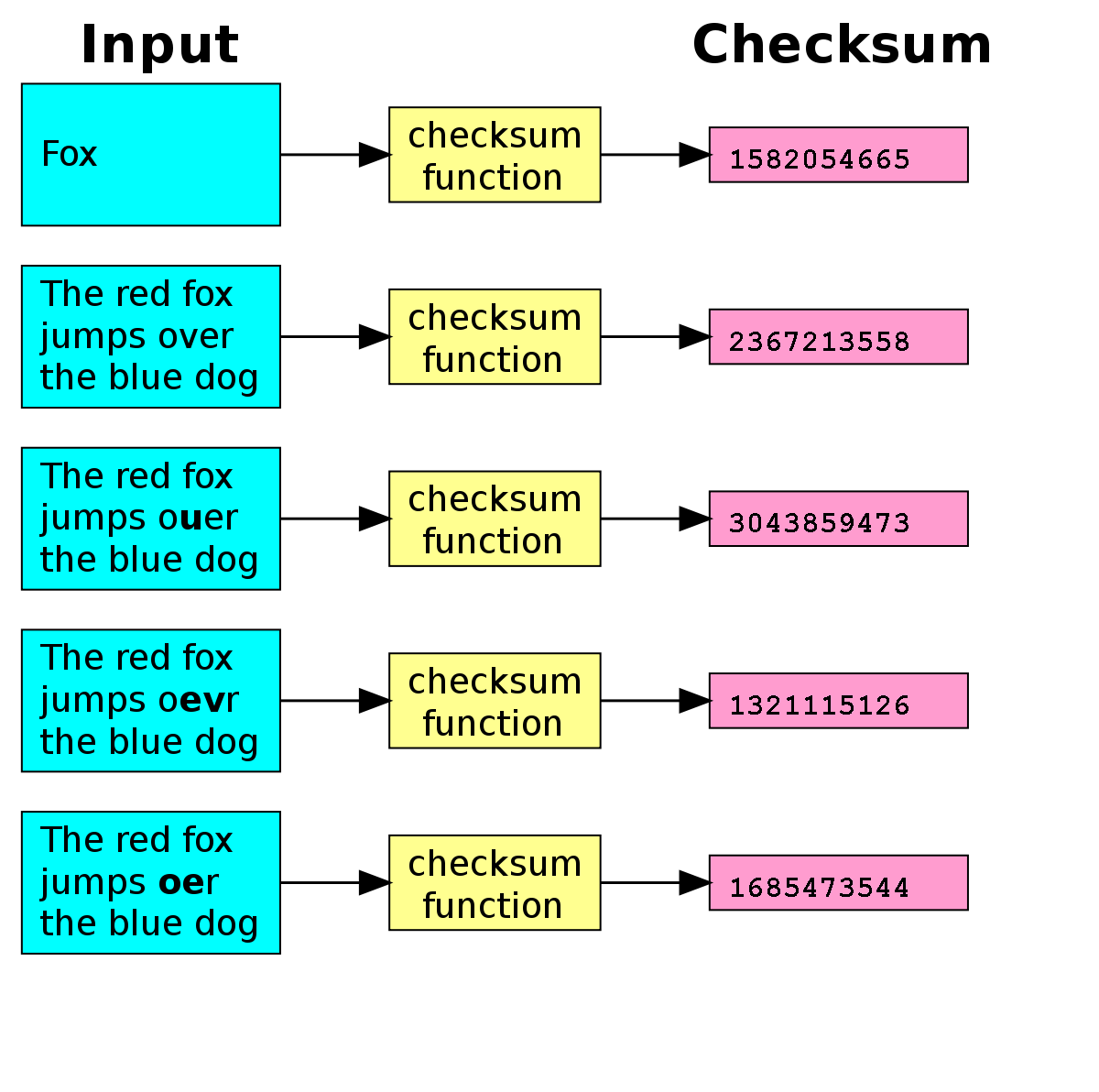
Alot of terminology is interchangeable:
A hash function maps some data to other data. It is often used to speed up comparisons or create a hash table. Not all hash functions are secure and the hash does not necessarily changes when the data changes.
A cryptographic hash function (such as SHA1) is a checksum that is secure against malicious changes. It is pretty hard to create a file with a specific cryptographic hash.
To make things more complicated, cryptographic hash functions are sometimes simply referred to as hash functions.
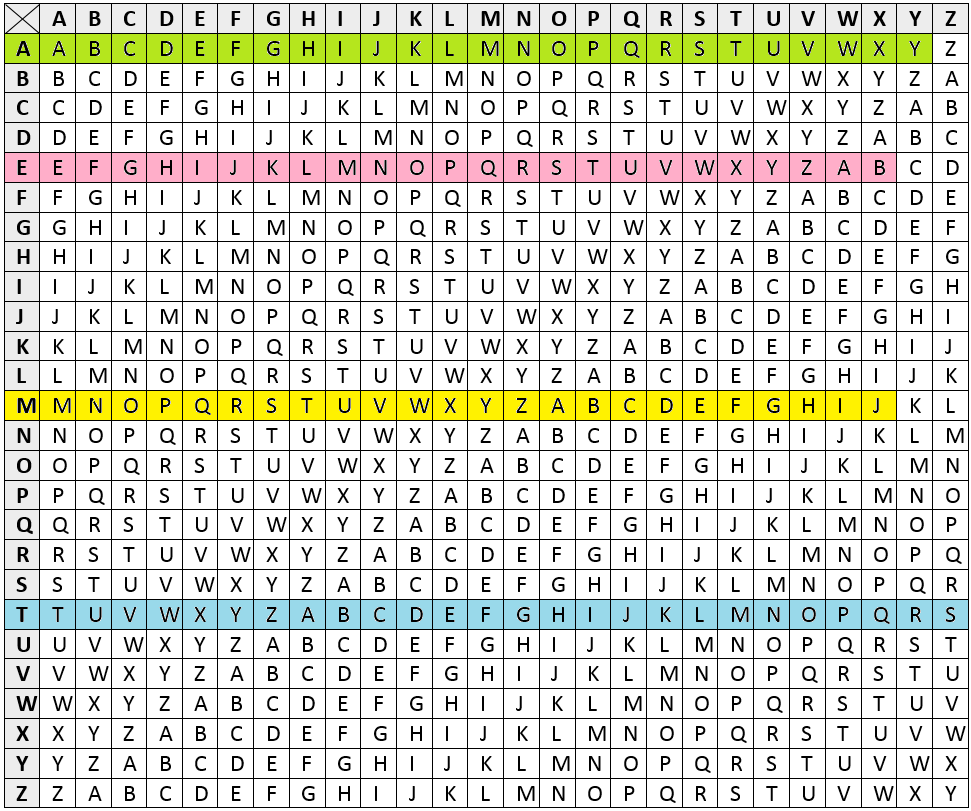
All of the following block ciphers, including Caeser and Vigenère, are symmetric.
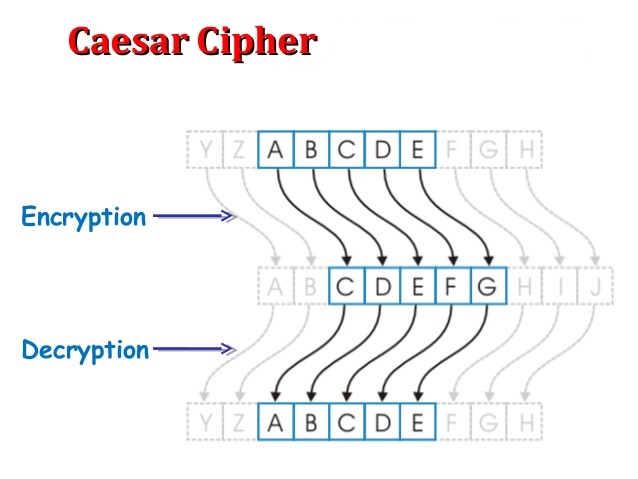
- one of the easiest methods to use in cryptography and can provide minimum security to the information (good for children or persons who have very little experience with security and encryption)
- use of only a short key in the entire process
- one of the best methods to use if the system cannot use any complicated coding techniques
- requires few computing resources and can be done easily with a pen and paper
- simple structure usage
- can only provide minimum security to the information
- frequency of the letter pattern provides a big clue in deciphering the entire message
- due to the nature of the cipher, an encrypted number sequence has only 10 possibilities with a common key or shift to all numbers.
A block cipher takes a block of plaintext bits and generates a block of ciphertext bits, generally of same size:
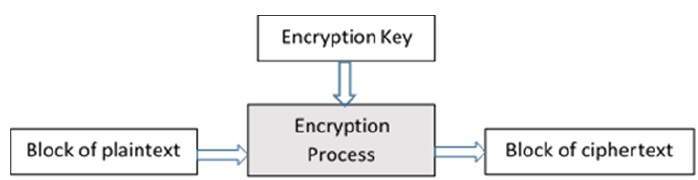
plaintext = "MATE"
ciphertext = "JYSB"
Well known symmetric block ciphers:
- Triple DES
- Encrypts data 3 times using a different key at least once – very slow. Good for PINs in ATMs
- Blowfish
- efficient open source algorithm for application encryption
- splits message into 64 bit blocks and encrypts each block individually
- Twofish is very similar but uses 128-bit blocks
- AES
- US Government Advanced Encryption Standard (128, 192 or 256 bit) replaced DES (64-bit) in year 2000
- each key is 128 bits long = 2^128 (combinations)
- each bit takes 10 math operations = 2^128 * 10 (total combinations)
- also available in 192 or 256 bits
Asymmetric encryption
Asymmetric cryptography uses DIFFERENT KEYS:
- to encrypt (public_key)
- to decrypt (private_key)
Both keys are 'linked' mathematically but it is computational infeasible to calculate the private key from the public key. This is slower but more secure encryption than symmetric cryptography. Public/private key encryption is a viable encryption method that could be used in the transmission of data between a secured section of a website and an end user.
A well-known asymmetric block cipher:
- RSA
- Public key to encrypt
- Private key to decrypt
- Widely used in internet and network security
- Used in every website you visit with HTTPS: (not always any more)
- HTTPS uses Secure Socket Layer (SSL) to encrypt data transfers between client and server
- SSL uses the RSA algorithm
recognise and describe features of symmetric (Data Encryption Standard — DES, Triple DES, AES — Advanced Encryption Standard, Blowfish and Twofish) and assymetric (RSA) encryption algorithms
no coding these, just be able to recognise and describe as per the next slide.
| Binary | ||||
|---|---|---|---|---|
| Base 2: [0,1] | ||||
| 23 | 22 | 21 | 20 | |
| 8 | 4 | 2 | 1 | |
| 1 | 0 | 1 | 1 | |
| equals 8 + 2 + 1 = decimal 11 (or in hexadecimal: 'b') | ||||
In other words, each hexadecimal digit (base 16) can represent four binary digits:
| Hexadecimal | ||||
|---|---|---|---|---|
| Base 16: [0,1,2,3,4,5,6,7,8,9,a,b,c,d,e,f] | ||||
| 163 | 162 | 161 | 160 | |
| 4096 | 256 | 16 | 1 | |
| b | 8 | |||
| equals 16*b(11) + 8 = 176 + 8 = decimal 184 | ||||